RBAC: IdP groups integration¶
You can now assign RBAC policies to user groups obtained from the external IDP. This change simplifies permissions management for external users without the need for unique sub IDs.
A user will be authorized to perform an operation if either their subject or any of the groups they belong to has the required permission. To use IdP groups in Percona Everest RBAC, you would need to set up the groups claim in your IdP provider configuration.
OKTA¶
Let’s consider you have successfully set up an Identity Provider (IdP) integration with Okta. In this configuration, the issuer URL identifies your API server, which acts as a unique identifier for your server within Okta. Additionally, you will have a client application, referred to as the Application integration, which is represented by the client ID. This setup allows for secure communication and authentication between your application and Okta’s services.
-
Navigate to Security > API.
-
In the list, find the API server that you use and click on Edit.
-
Click Scopes > Add Scope.
Note
A Scope describes the information that potentially can be requested.
Add a scope called groups and keep all other options set to their default values.
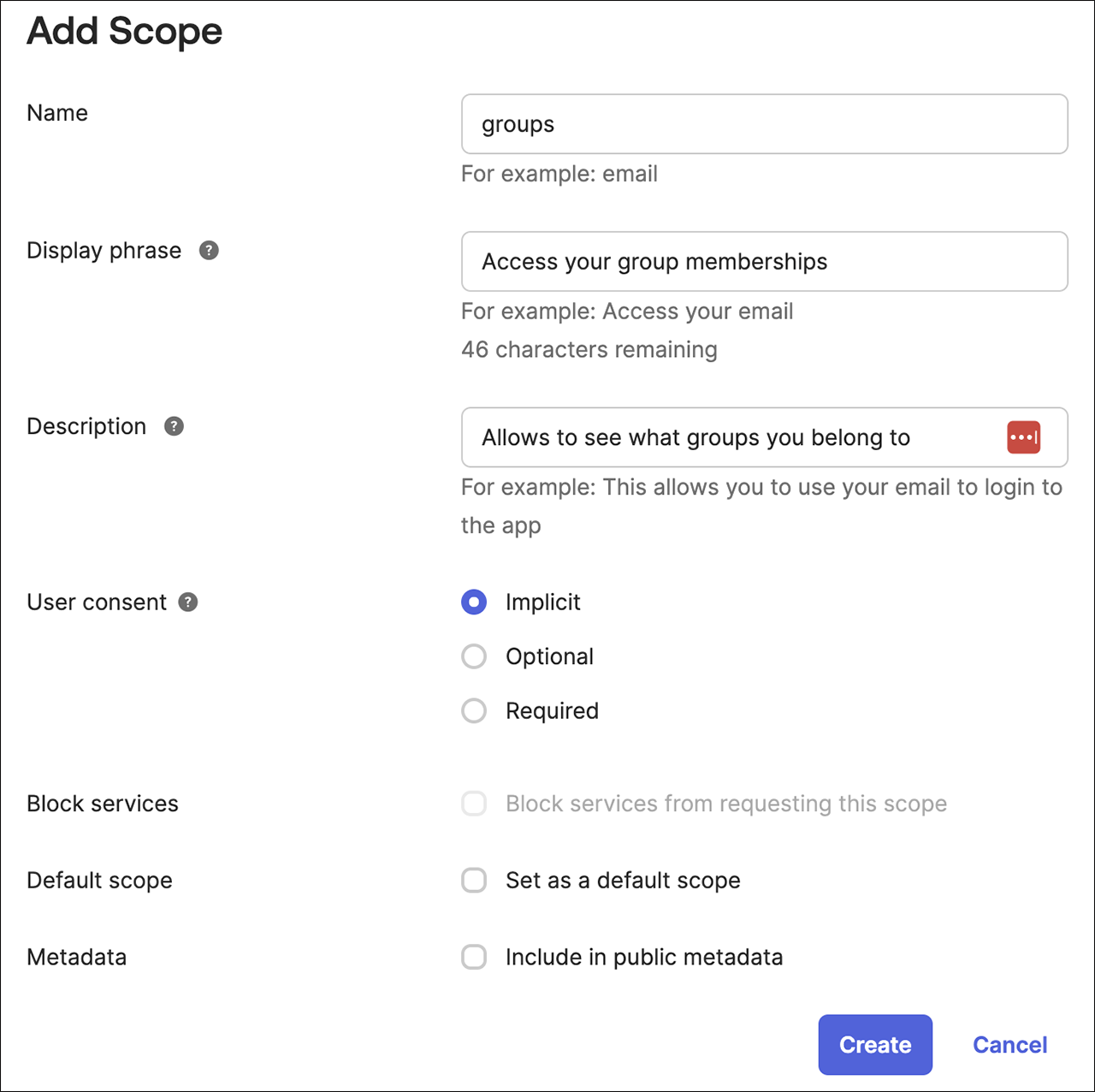
-
Click Claims > Add Claim.
Note
A claim specifies the scope to activate and the information required within that scope.
-
Add a claim named groups.
-
Set the Include in token type to ID Token and choose Always.
-
Change the Value type to Groups.
-
Select Filter as Matches regexp and add a filter to match the desired Okta groups for Everest, for example: .*.
-
Set Include in to groups, which is the scope you created earlier.
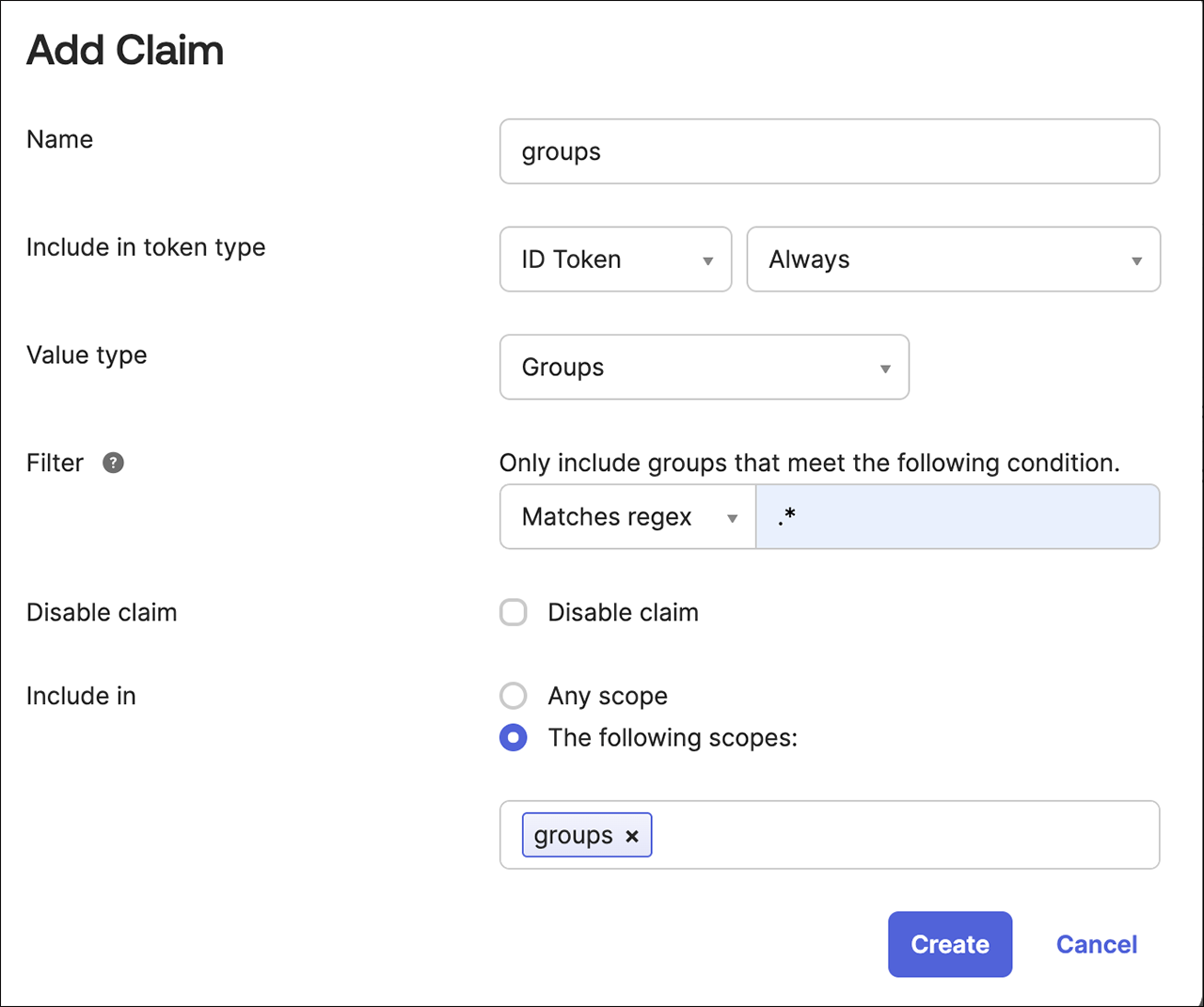
-
-
Click Create.
-
Click Access Policies > Add Policy. A policy restricts how this authorization server is used.
-
Add Name and Description.
-
Assign the policy to the client (Application Integration) you created earlier. The field should auto-complete as you type. Create the policy.
-
Create the policy.
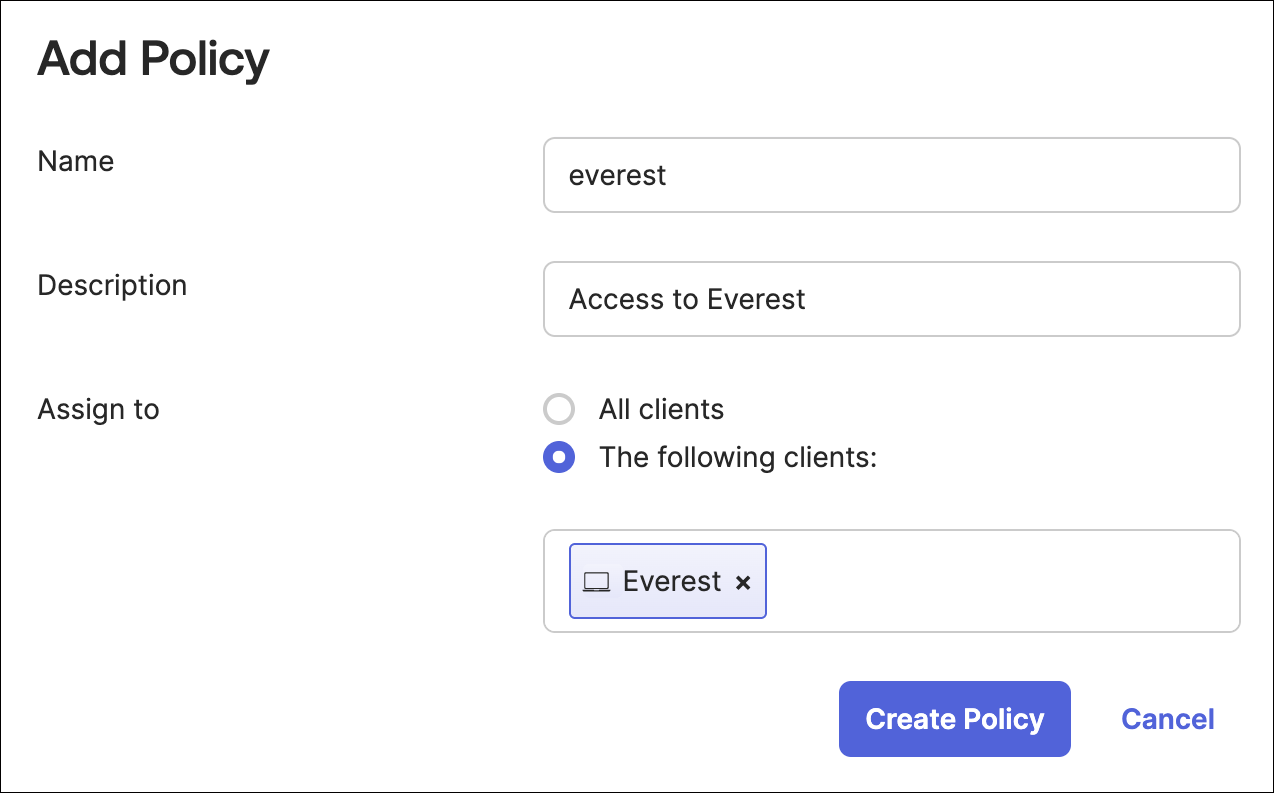
-
-
Add a rule to the policy. A Rule defines the details of usage:
-
Add a name. If you prefer, you can use default option.
-
Fine-tune the settings to align with your organization’s security policy. Here are some suggestions:
- Uncheck all grant types except for the Authorization Code.
- Adjust the token lifetime to determine how long a session can remain active.
- Restrict the refresh token lifetime or consider deactivating it completely.
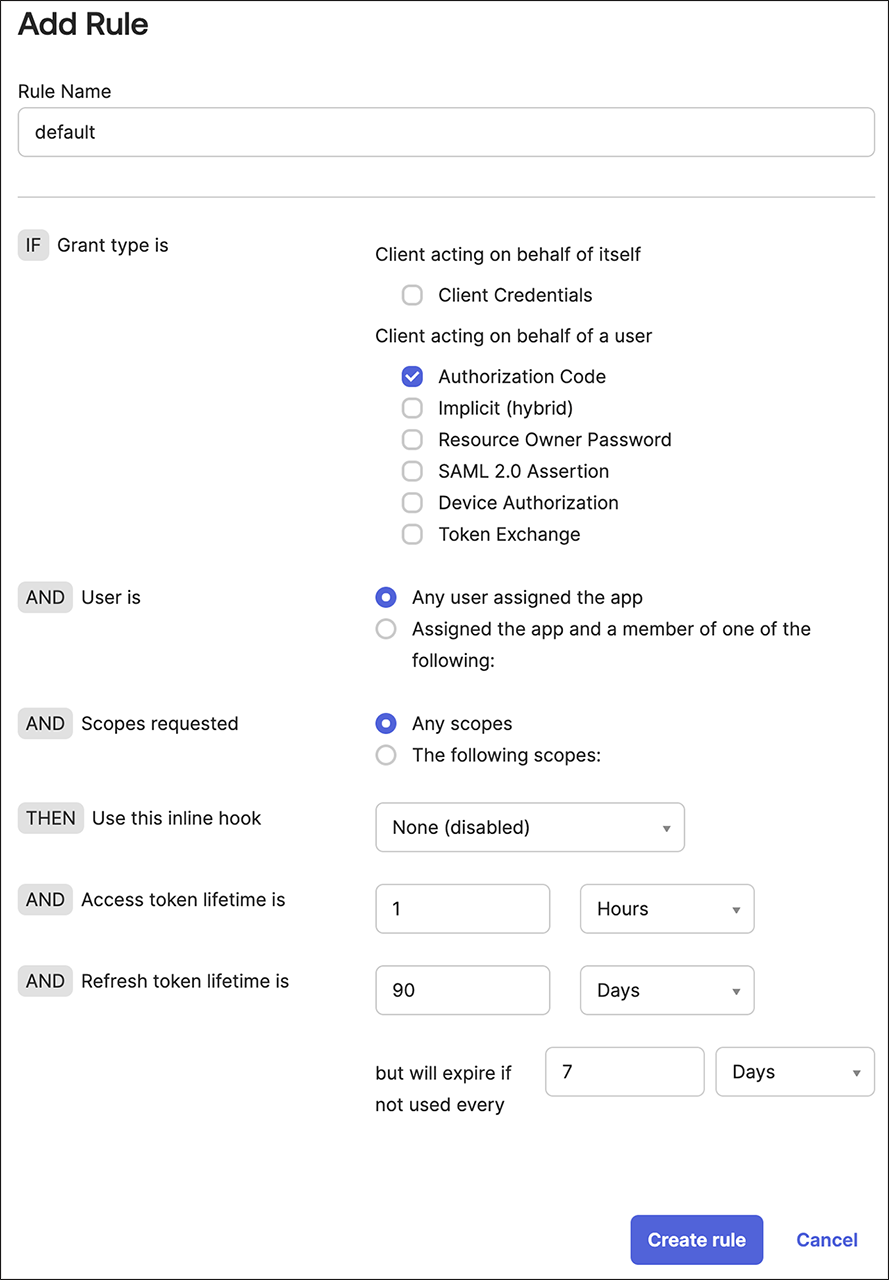
-
-
Click Create Rule.
Get expert help¶
If you need assistance, visit the community forum for comprehensive and free database knowledge, or contact our Percona Database Experts for professional support and services.